Application logs
Providers of OpenFin applications can have unique, separate logs for each application. App providers can retrieve these logs for later use. When this feature is enabled, anything that the app writes to the console goes to a separate folder and log file in the OpenFin installation directory. With OpenFin app log management, app providers can encrypt and deliver their logs to a remote location managed by OpenFin. Log owners are able to download and decrypt their logs with a private key via OpenFin’s Log Manager API.
Note:
Starting in OpenFin version 40, you can use the Log Uploader tool to send logs to a server maintained by your organization.
This option is an alternative to sending and retrieving logs using OpenFin's server, as described in this article.
How it works
When an app outputs message to the console, that message is written to a log file in the RVM’s installation directory, in the app’s subfolder.
Examples: console.log, console.info, console.warn, console.error
-
Console output is queued by the runtime and written periodically to a log file by the RVM.
-
When the application closes, the RVM compresses the most recent app log file and places it in an archive folder in the app’s subfolder under the RVM’s installation directory; it then uploads the compressed file to the log manager server.
-
Alternatively, logs can be sent on demand via the runtime API
sendApplicationLog(available in runtime 10+) (RVM 4.6+) -
(Optional) Logs can be associated with a developer-specified username in order to retrieve app logs by a specific username using the
setAppLogUsernameruntime API (RVM 4.6+, Runtime 9.61.37.46+). If a username is set, logs for the session can be retrieved by username via the Log Management Service. -
Log message timestamps use the local time by default, in the format
y-MM-dd HH:mm:ss.SSS. Starting in Runtime version 38, you can specify that timestamps use UTC, via theappLogTimezonemanifest property. If that property is defined (as either "utc" or "local"), timestamps use ISO 8601 format. -
Creation of application logs is enabled by default. If you prefer to disable app logs, set
enableAppLoggingto false in the application manifest.
Enable log retrieval
Log management requires RVM 4.4.0.13+ and a valid OpenFin licenseKey.
Sample app manifest to enable log management:
{
"licenseKey": "VALID_LICENSE_KEY",
"runtime": {
"version": "AA.BB.CC.DD"
},
"startup_app": {
"name": "APPLICATION_NAME",
"uuid": "APPLICATION_UUID",
"url": "http://EXAMPLE.COM:8000/index.html",
"enableAppLogging": true,
"appLogsTimezone": "utc",
"logManagement": {
"enabled": true,
"encryptionKey": "RSA_PUBLIC_KEY"
}
}
}
Storage
All logs are stored on AWS S3 in the us-east-1 region replicated in multiple zones and us-west-1 for increased availability. Data in S3 is encrypted by Amazon. If encryption is enabled, a private key set by the desktop is required to view the logs in human-readable form. OpenFin never deletes the logs; only the customer deletes logs.
API keys
Please contact [email protected] to get an API key.
Encryption
To encrypt application logs, the App Provider needs to create a public and private RSA key pair, and supply the public key in the app manifest as the startup_app.logManagement.encryptionKey property, encoded in base64.
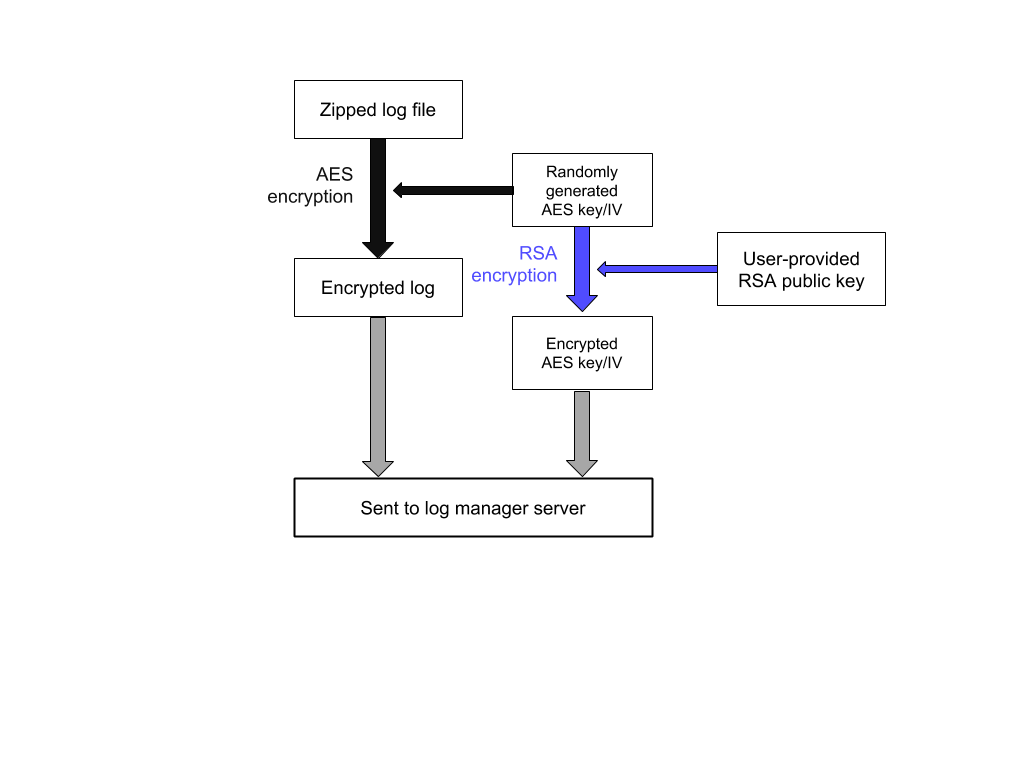
The following procedure is followed for encryption of the zipped log file:
-
An AES-256-CBC key K and initialization vector IV are randomly generated.
-
K and IV are used to encrypt the file, resulting in the ciphertext C_F.
-
K and IV are encrypted with the user’s RSA public key using RSAES-OAEP with SHA-1, resulting in the encrypted key C_K, and encrypted initialization vector C_IV.
-
C_F, C_K, and C_IV are uploaded to the log manager.
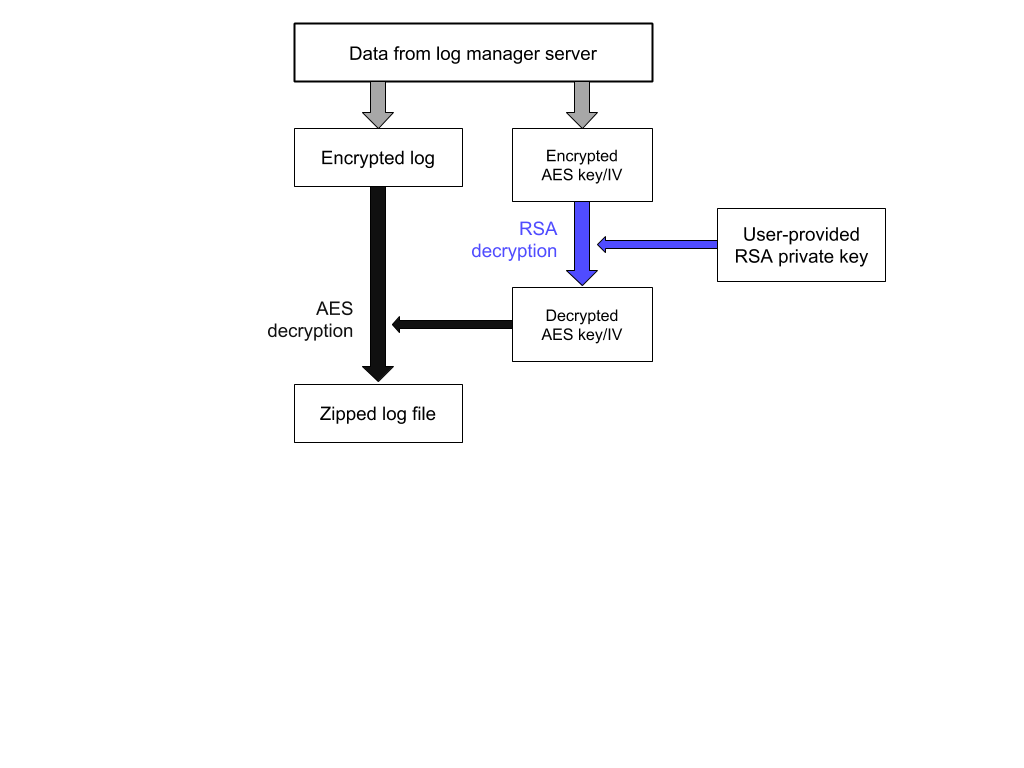
The decryption process is as follows:
-
C_F, C_K, and C_IV are retrieved from the log manager with a
GETrequest. -
C_K and C_IV are decrypted with the user’s RSA private key, giving the decrypted K and IV.
-
K and IV are used to decrypt C_F, giving the decrypted file.
Encryption workflow
Decryption workflow
Updated 2 months ago
